Why Democratizing Automation Fails: Implementing The Tiered Governance Protocol
The prevailing narrative in the no-code space is overwhelmingly optimistic: "Democratize automation." The pitch is that by giving every employee a license to Zapier or Make, you unlock a wave of grassroots innovation that eliminates inefficiency from the bottom up. While the intention is noble, the reality for the Internal Ops Manager is often a chaotic sprawl of "Shadow IT."
In my observation of teams scaling their operations, total democratization doesn't lead to efficiency; it often leads to fragility. When everyone is a builder, documentation vanishes, naming conventions are ignored, and critical processes break the moment a specific employee goes on vacation or leaves the company.
This article argues for a contrarian approach: Restricting build access to preserve system integrity.
I call this structure The Tiered Governance Protocol. It is a framework designed to balance the need for speed with the absolute necessity of reliability.
The Problem with "Citizen Development"
To be clear, I am not against empowering employees. However, I have noticed that without strict guardrails, "citizen development" creates three specific liabilities:
- Orphaned Scenarios: An employee builds a critical notification bot on their personal account. They leave the company. The credit card fails. The process stops. IT has no access.
- API Thrashing: Inexperienced builders often create loops that hammer API limits, causing company-wide outages on shared connectors like Slack or Jira.
- Data Leaks: Without understanding webhooks or JSON payloads, it is surprisingly easy to accidentally expose sensitive internal data to external endpoints.
The Solution: The Tiered Governance Protocol
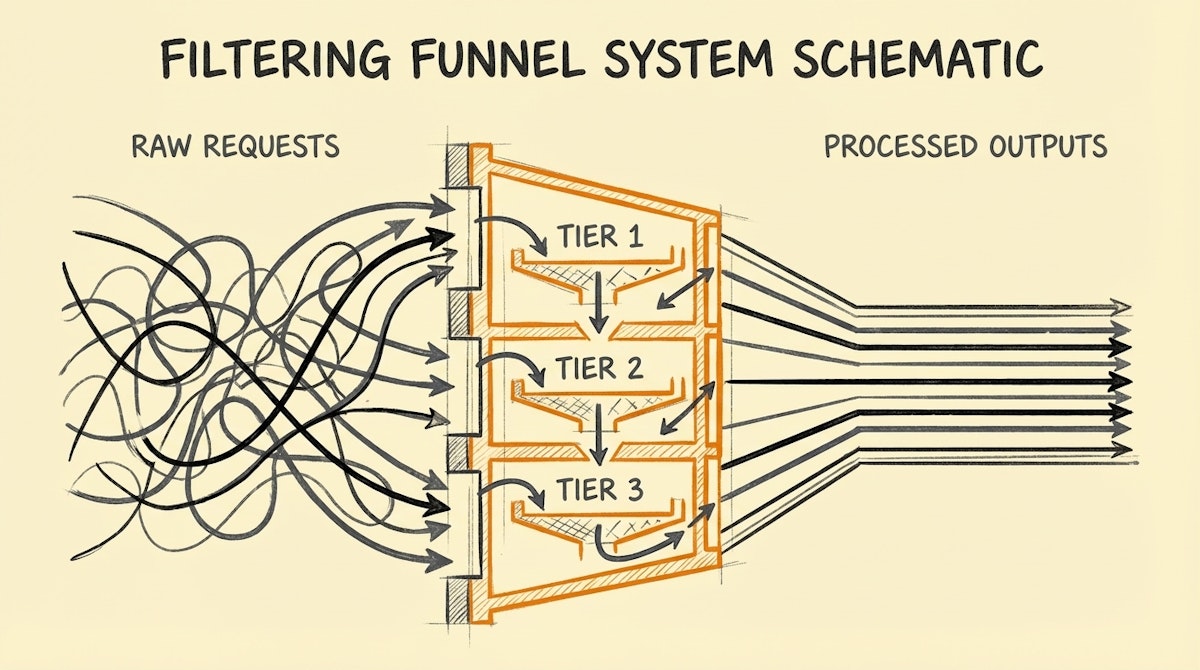
Instead of a flat structure where everyone has Admin or Builder permissions, this protocol divides the organization into three distinct tiers. This ensures that innovation happens within a safety net.
| Role Tier | Access Level | Responsibility |
|---|---|---|
| Tier 1: The Requester | Trigger Only | Identifies pain points; submits requests via formal channels. |
| Tier 2: The Certified Builder | Sandbox / Draft | Builds prototypes; must pass an internal "certification" on naming/error handling. |
| Tier 3: The Architect (Ops) | Production Deploy | Audits logic; merges to production; manages API keys. |
Phase 1: The Intake Airlock
The first step in regaining control is channeling enthusiasm. Rather than letting Tier 1 employees build solutions immediately, they should be directed to an Intake Airlock.
I often recommend using an Airtable form as the front end. The employee submits the problem they are trying to solve, not the automation they want to build. This distinction is crucial. It allows the Ops team (Tier 3) to determine if automation is even the right solution, or if the process itself is flawed.
Phase 2: The Certification Sandbox
For those employees who genuinely want to build (Tier 2), simply handing over the keys is risky. A safer approach is to establish a "Sandbox Team" environment within your automation platform (feasible in Make's Enterprise or Teams plans).
In this environment, Tier 2 builders can experiment. However, I suggest implementing a hard rule: No Tier 2 builder can deploy to Production.
To move a scenario from Sandbox to Production, it must pass a code review covering:
- Error Handling: Are there "Break" or "Resume" directives?
- Documentation: Is every module labeled with a description?
- Efficiency: Is the logic burning unnecessary operations?
Phase 3: The Production Handover
Once a workflow is vetted, ownership transfers to the central Ops team (Tier 3). This effectively solves the "Orphaned Scenario" problem. The automation no longer belongs to the individual; it belongs to the infrastructure. If the creator leaves, the system remains stable.
Why Friction is Necessary
Implementing this protocol adds friction. Ops Managers will likely face pushback from teams who feel their agility is being stifled. However, in the context of scaling internal operations, friction is a feature, not a bug. It prevents the deployment of half-baked logic that generates technical debt.
| Metric | Open Access Model | Tiered Governance Protocol |
|---|---|---|
| Speed to Deploy | Fast (Hours) | Moderate (Days) |
| Maintenance Load | High (Reactive fixing) | Low (Proactive auditing) |
| System Reliability | Unpredictable | Stable |
Conclusion
The goal of the Ops Manager is not to prevent automation, but to professionalize it. By implementing The Tiered Governance Protocol, you shift the culture from one of "move fast and break things" to "move deliberately and build things that last." It protects the organization from the silent accumulation of error-prone workflows and ensures that automation remains a strategic asset rather than a liability.
